Windows Hello for Business🔗︎
Issue: Windows needs your current credentials🔗︎
This message pops up within a few seconds of logging in with a PIN, seamingly randomly during use and it also manifests itself when attempting to access AD domain-joined resources such as file shares. Windows 10 devices don't appear to have an issue.
I haven't been able to find a single article that helps. I expect most articles are aimed at Windows Hello as opposed to Windows Hello for Business. Lets hope this one does 
Pressing CTRL+ALT+DEL >> Lock >> Sign-option >> and entering your password does allow one to connect to remote resources for a period of time.
Environment🔗︎
My Windows EUC devices are all Entra ID (AAD) joined, however I have local servers that are AD joined. This is a hybrid environment. Windows Hello for Business has been configured. This issue only seems to impact Windows 11 devices. I am writing this post agains Windows 11 Enterprise 23H2.
| Deployment model | Hybrid | On-prem and Entra ID resources |
| Trust type | Key | |
| Device Config | GPO (local) | No MDM / Puppet / DSC |
| Auth to Entra ID | Cloud authentication | Password hash sync (PHS) or Pass-through authentication (PTA) |
https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/deploy/
Cloud Kerberos required Sever 2022+ Migrate DC to Server 2025: https://www.petenetlive.com/kb/article/0001884
Troubleshooting.🔗︎
As the error pops up when accessing remote resources, my guess is there may be an issue with Kerberos ticketing.
Cracking open Event Viewer revealed two logs.
This entry was in the logs around the time of the first "Windows needs your credentials..." message pops up, but it doesn't repeat every time.
Log Name: System
Level: Error
Source: Security-Kerberos
User: N/A
OpCode: Info
Event ID: 11
Text:
The Distinguished Name in the subject field of your smart card logon certificate
does not contain enough information to identify the appropriate domain on an
non-domain joined computer. Contact your system administrator.
Logged when attempting to access a remote system and the "Windows needs your credentials..." message pops up.
Log Name: System
Level: Warning
Source: LSA (LsaSrv)
User: SYSTEM
OpCode: Info
Event ID: 40960
Text:
The Security System detected an authentication error for the server
cifs/{remote_computer}. The failure code from authentication protocol
Kerberos was "The client certificate does not contain a valid UPN,
or does not match the client name in the logon request.
Please contact your administrator.
(0xc00002f9)".
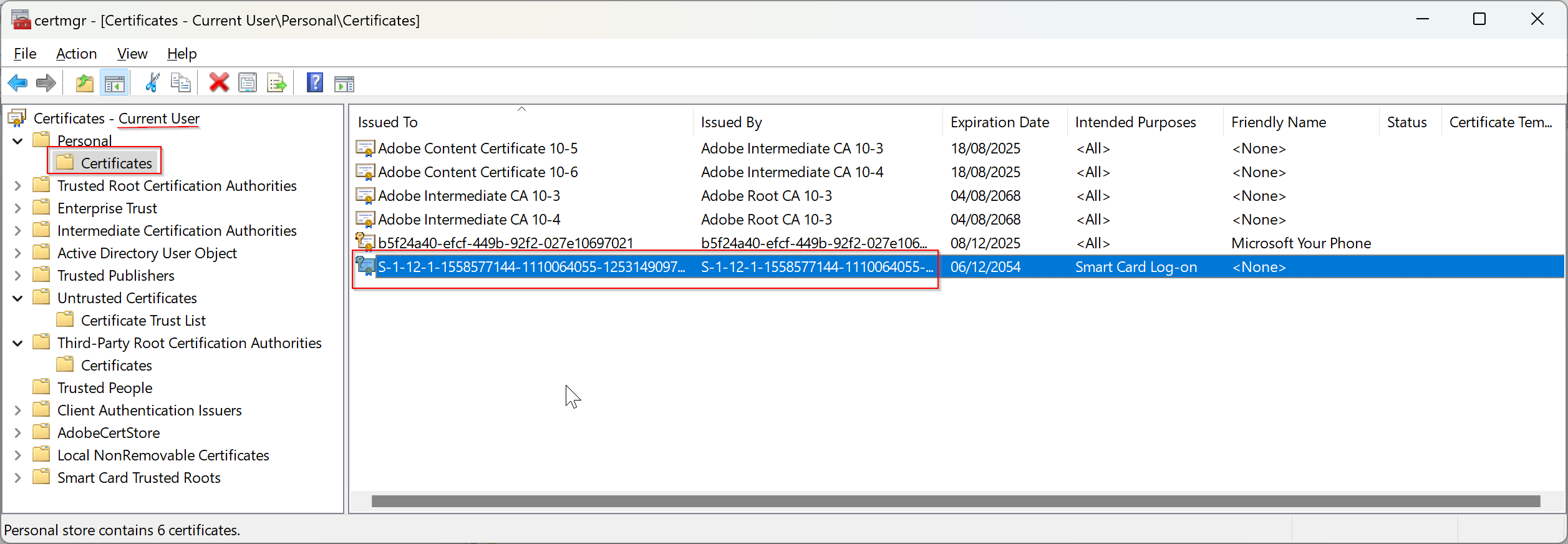
Using the info from Event ID: 11, crack open certmgr.msc and have a look for the "Smart Card Logon" certificate.
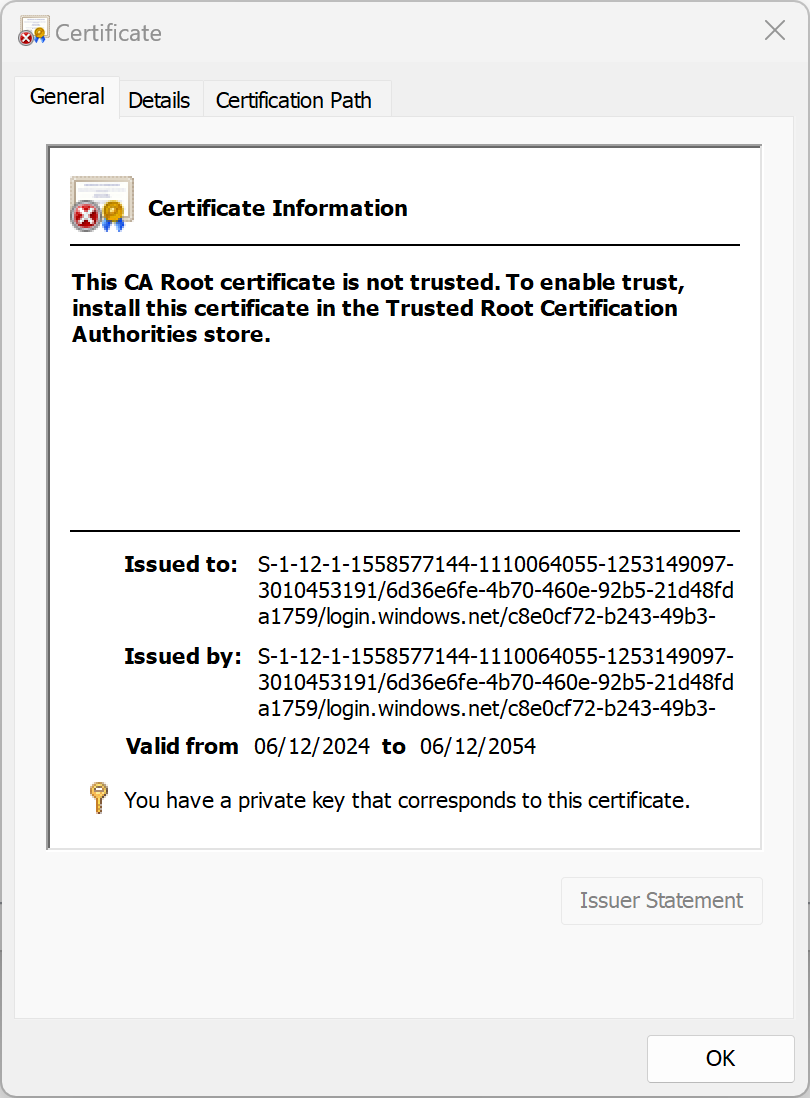
This doesn't look right, but looking at the same certificate on a Windows 10 machine, they're very similar. Let's see what Google has to say on the matter:
if your client machines are AADJ (cloud joined). They trust your domain name present by the KDC certificate your KDC certificate should contain subject with "Distinguishname" -where it can extract "DC=contoso, Dc=Com" i.e if your domain is contoso.com Else if you have CA template 2012R2 and above , default Subject alternative names populate domain name in it. i.e dns name =DC1.contoso.com , DNS name =contoso.com
we already listed this in our known issue (I was the one updated the doc :)) . This would often happen if they used third party CAs too.
The page referenced in the above quote suggests to look in the client's event logs (Application and Services/Microsoft/Windows/Security-Kerberos/Operational).
Enable log
The Microsoft article suggests this log is disabled by default. To enable it. In Event Viewer, right-click Operational and click Enable Log.
It's probably a good idea to disable once finished as it seems rather chatty.
Logging in / unlocking and attempting to access remote resources that generates the "Windows needs your credentials..." message did not generate event ID 107, but I do get event ID 201:
Log Name: Microsoft-Windows-Security-Kerberos/Operational
Level: Warning
Source: Security-Kerberos
User: SYSTEM
OpCode: Info
Event ID: 201
Text:
Attempt to use Kerberos unconstrained delegation failed.
Target server: cifs/{windows_file_server}
Supplied user: NULL
Supplied domain: NULL
PID of client process: 4
Name of client process:
LUID of client process: 0x3E7
User identity of client process: {client_pc}0$
Domain name of user identity of client process: WORKGROUP
Mechanism OID: 1.2.840.48018.1.2.2
Kerberos unconstrained delegation is not allowed for this user.
For more information, see https://go.microsoft.com/fwlink/?linkid=856824.
Important🔗︎
Remove credential guard https://learn.microsoft.com/en-us/windows/security/identity-protection/remote-credential-guard?tabs=gpo